Private vs. public cloud security: Benefits and drawbacks
Uncover the differences between private vs. public cloud security -- as well as hybrid cloud security and multi-cloud security -- before deciding on an enterprise deployment model
Regardless of whether an enterprise's infrastructure operates in a private, public, hybrid cloud or multiple clouds, cybersecurity is a critical component. Some cloud architectures greatly simplify security tasks and tool integrations, but that often comes at the cost of flexibility.
Let's look at the benefits and challenges organizations face as they compare private vs. public cloud security, as well as hybrid cloud security and multi-cloud security, in 2024 and beyond.
Private cloud security
As its name implies, private clouds grant a business private access to dedicated infrastructure resources within a cloud. This infrastructure has both advantages and disadvantages.
Private cloud security benefits
Private clouds are attractive to organizations seeking more granular control over the underlying infrastructure. This commonly includes customer configuration access to the network, OSes and server virtualization platform.
This article is part of
What is cloud security management? Guide and best practices
From a security perspective, private cloud's advantages include the following:
- Better control. In-house administrators have more flexibility when it comes to implementing and accessing security tools.
- Complete visibility. With private cloud, the business gains full control and visibility over its cybersecurity posture and can customize it to fit its specific needs.
Private cloud security drawbacks
The flexibility of private cloud comes at a cost in two areas: pricing and management.
- Financial costs. Operating private clouds is often a more expensive endeavor than public cloud options. Businesses pay a premium for granular cloud control and visibility.
- Managerial costs. Designing and maintaining cybersecurity tools inside private clouds dramatically increases management responsibilities.
For these two reasons, it is critically important that IT decision-makers carefully weigh the cybersecurity benefits of private clouds against the added financial expenses and management overhead.
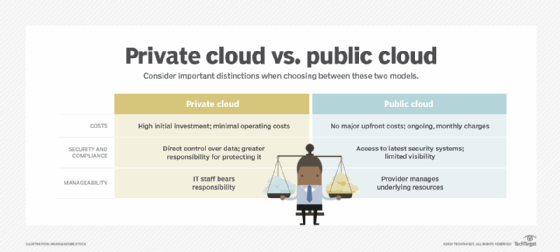
Public cloud security
Organizations can employ third-party cloud service providers (CSPs) to manage applications and data within their data center infrastructure. Many CSPs also provide built-in security tools to help protect business-critical data.
Public cloud security benefits
Businesses are attracted to public cloud infrastructures for a variety of reasons, including low Capex, service scalability and easing the management workload for in-house IT staff.
Public cloud model security benefits include the following:
- Lightening the load. Larger CSPs often invest heavily in top-end cybersecurity tools, as well as staff who are highly knowledgeable in their field. This makes offloading cybersecurity tools and tasks from in-house to a third party appealing.
- Addressing the cybersecurity skills gap. The ability to defer to a CSP's security program reduces the need to hire expensive and scarce in-house infosec talent.
Public cloud security drawbacks
Other businesses, especially larger ones with massive IT infrastructures, might find that public cloud security is not the right fit.
Potential public cloud security challenges include the following:
- CSP security is not up to par. In some situations, organizations might determine that a CSP's cybersecurity tools, processes and methods are insufficient for protecting highly sensitive data.
- Inadequate visibility. Larger organizations often require the ability to obtain and analyze logs, alerts and other data down to the packet level. For many CSPs, especially those that deal with SaaS, much of this security information is not accessible to customers. This is because most of the underlying technologies have been abstracted to simplify management from a customer perspective.
Hybrid cloud security
In hybrid cloud environments, some business applications and data reside in public clouds, while others are managed inside private clouds or private data centers.
Hybrid cloud security benefits
With hybrid cloud, the whole might be greater than the sum of its parts. Security advantages of hybrid cloud infrastructure include the following:
- Best of both worlds. Hybrid cloud enterprise architectures combining the best features of public and private cloud can provide the utmost security.
- Flexibility. Hybrid models give administrators the power to decide where applications and data reside, such as in a cloud or corporate data center.
Hybrid cloud security challenges
Like with a private cloud, the flexibility of a hybrid cloud infrastructure has its downsides. For example, decisions about where applications and data reside are a significant responsibility and require deliberation.
Organizations should consider the following potential security disadvantages of the hybrid cloud model:
- Policy enforcement challenges. Cybersecurity policies can become difficult to duplicate and extend across public and private clouds, as well as on-premises data centers. In some cloud architectures, such as SaaS, it might be impossible to duplicate a security policy found in other parts of a corporate infrastructure.
- Security inconsistencies. Because of policy enforcement issues, some applications and data might not be as secure as others.
- More skills required. Security administrators must deal with differing methods and tools to monitor and act on threats depending on where vulnerable resources reside.
Multi-cloud security
As the name suggests, a multi-cloud environment involves an organization using two or more cloud platforms or vendors. For example, an organization might use AWS for IaaS, Google App Engine for PaaS, and Microsoft 365 and Salesforce SaaS applications.
Multi-cloud security benefits
As in hybrid environments, multi-cloud deployments enable admins to put applications and data into the service with the most appropriate security levels. Similarly, they can adopt the most secure cloud offerings across CSPs.
Multi-cloud environments also offer the following security benefits:
- Cyber resilience. Multi-cloud deployments enable organizations to distribute data across more than one cloud. If an event occurs on one service, such as an outage or security event, operations can shift to another cloud, so that data and applications are still accessible. This helps eliminate single points of failure and maintain constant security, even if one has an issue.
- Disaster recovery and business continuity. Improved cyber resilience helps improve DR/BC processes. Because data, applications and other operations are accessible across different clouds, business operations aren't halted.
Multi-cloud security drawbacks
Like hybrid cloud security challenges, multi-cloud environments require close management and consideration to decide where applications and data should reside. It can be difficult to apply a single security policy across multiple clouds, which can create security gaps. Using multiple clouds also requires security teams to know how to secure each cloud, as well as the best tools to use.
Multi-cloud deployments are also prone to the following security challenges:
- Configuration management. Many cloud breaches are traced back to misconfigurations. Configuration management across multiple clouds -- especially when it requires multiple, disparate tools -- is difficult.
- Visibility. A single public cloud has inadequate visibility. Multiply that by the total number of clouds in use, and visibility challenges can be overwhelming. Coordinating monitoring and alerting across clouds requires specific skills and tools.
- Incident detection and response. Creating and enforcing an incident response plan across multiple clouds can require multiple playbooks, workflows and tools, as well as incident responders with skills across each cloud service.
- Regulatory compliance. Organizations in specific industries might have difficulty meeting compliance requirements, especially given the separation of duties with CSPs in the shared responsibility model.
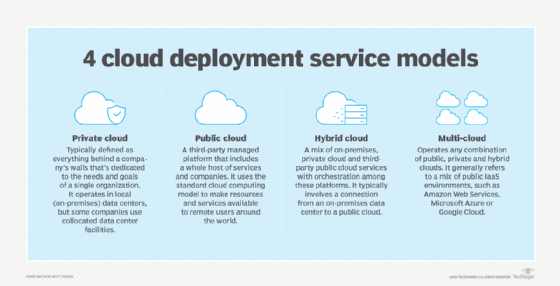
How to determine the best cloud security option
With these challenges in mind, remember that many infrastructure security tools are now largely virtualized. This means the same security tools and policy configurations deployed within in-house data centers and across the corporate LAN can extend to private clouds to achieve hybrid or multi-cloud security parity. For many security departments, this greatly reduces security complexity from a uniformity point of view.
When it comes to cloud computing and cloud security, no single architecture is suitable for all businesses. IT architects must gauge the cybersecurity needs for all business applications and data sets. Once defined, the technology services can be categorized and earmarked for deployment in the public or private cloud -- whichever makes the most sense both from a cost and cybersecurity perspective.
Andrew Froehlich is founder of InfraMomentum, an enterprise IT research and analyst firm, and president of West Gate Networks, an IT consulting company. He has been involved in enterprise IT for more than 20 years.
Sharon Shea is executive editor of TechTarget Security.







